The Dawn of a New Digital Conflict: AI Against AI
In the sprawling, invisible landscape of cyberspace, a new kind of war is brewing. This conflict isn’t waged by human hackers in dimly lit rooms, but by autonomous, intelligent algorithms operating at machine speed. We have entered the era of the algorithmic arms race, where offensive artificial intelligence, designed to probe, adapt, and attack, is pitted against defensive AI, engineered to predict, detect, and neutralize threats in real-time. This AI vs. AI paradigm represents the most significant shift in cybersecurity since the invention of the firewall. The stakes are no longer just about protecting corporate data; they involve the security of our entire connected world, from critical infrastructure to the intimate devices in our homes. As we see in the latest AI Research / Prototypes News, laboratories are actively developing both sides of this equation, forcing a rapid evolution in how we approach digital defense. This article delves into this emerging battlefield, exploring the capabilities of offensive AI, the innovations in defensive AI, and the strategic imperatives for navigating this new reality.
Section 1: The New Battlefield: Offensive vs. Defensive AI Paradigms
The core of this new conflict lies in the fundamental asymmetry of cybersecurity: attackers only need to find one vulnerability, while defenders must protect every possible entry point. AI is amplifying this dynamic on both sides, creating a high-speed, high-stakes environment where human intervention is often too slow to be effective. Understanding the capabilities and philosophies behind both offensive and defensive AI is crucial to grasping the scope of this new arms race.
What is Offensive AI?
Offensive AI refers to the use of machine learning and autonomous systems to automate and enhance cyberattacks. These are not simple scripts; they are learning systems designed to operate with a level of sophistication and speed that surpasses human capabilities. Key applications include:
- Automated Vulnerability Discovery: AI models can be trained on vast codebases to identify novel, or “zero-day,” vulnerabilities far faster than human researchers. They can intelligently fuzz systems, feeding them malformed data to uncover exploitable crashes and weaknesses.
- Adaptive Malware: Imagine malware that can rewrite its own code (polymorphism) to evade signature-based antivirus detection. Offensive AI can create malware that analyzes its environment—the specific network, the security tools in place—and modifies its behavior to remain undetected.
- Hyper-Personalized Social Engineering: AI can scrape public data from social media and corporate websites to craft incredibly convincing phishing emails, text messages, or even deepfake voice calls. These attacks are tailored to the individual, making them exponentially more effective than generic campaigns. This is where AI Tools for Creators News intersects with security, as the same technology used for creative pursuits can be weaponized.
The targets for these systems are expanding daily. An offensive AI could coordinate an attack on a city’s power grid by targeting vulnerabilities in Smart City / Infrastructure AI Gadgets News, or launch a distributed denial-of-service (DDoS) attack using a botnet of compromised AI Sensors & IoT News devices, from smart thermostats to security cameras.
The Countermeasure: Defensive AI
In response, defensive AI leverages the same underlying technologies to build a proactive and resilient “cyber immune system.” Instead of relying on static rules and known threat signatures, it focuses on understanding normal behavior and identifying anomalies that signal an attack. Its primary functions include:

- Behavioral Analytics and Anomaly Detection: Defensive AI establishes a baseline of normal activity for users, devices, and networks. It can then instantly flag deviations—like a user accessing a server at 3 AM from a new location or an AI Security Gadgets News camera suddenly sending data to an unknown server—as potential threats.
- Predictive Threat Hunting: By analyzing global threat intelligence and internal network telemetry, AI models can predict likely attack vectors and identify precursor activities before a full-blown breach occurs. This shifts security from a reactive to a proactive posture.
- Automated Incident Response: When a threat is detected, an AI agent can take immediate action—quarantining an infected device, blocking a malicious IP address, or patching a vulnerability—in milliseconds. This speed is critical when battling an offensive AI that operates on a similar timescale. This technology is vital for protecting data from the latest Health & BioAI Gadgets News, where a breach could have life-threatening consequences.
Section 2: The Arsenal of Offensive AI: Techniques and Targets
The theoretical potential of offensive AI is rapidly becoming a practical reality. Research labs and malicious actors alike are prototyping systems that can execute complex attack chains with minimal human oversight. These tools don’t just find an open door; they analyze the building’s blueprints, pick the lock, and navigate the interior to find the most valuable assets.
Automated Reconnaissance and Exploitation
The first step in any sophisticated attack is reconnaissance. An offensive AI can scan an organization’s entire digital footprint—websites, cloud services, employee profiles on LinkedIn, code repositories on GitHub—to build a detailed map of potential weaknesses. It can then cross-reference this map with a database of known exploits and even use generative models to devise new attack paths. For example, it might discover an outdated software library used in a company’s mobile app, a critical finding in the realm of AI Phone & Mobile Devices News, and automatically deploy an exploit for it.
Case Study: A Coordinated Attack on a Smart Home
Consider a hypothetical scenario targeting a modern smart home. An offensive AI begins by identifying the home’s public IP address.
- Reconnaissance: It scans for open ports and identifies various connected devices: a smart TV, an AI Audio / Speakers News device, a security system, and even a Robotics Vacuum News cleaner.
- Initial Breach: The AI discovers a known, unpatched vulnerability in the smart speaker’s firmware. It exploits this to gain a foothold on the home’s Wi-Fi network.
- Lateral Movement: Once inside, the AI uses its access to scan the internal network. It identifies the homeowner’s laptop and uses its hyper-personalization engine to craft a fake security alert, seemingly from the smart speaker’s manufacturer, prompting the user to enter their network credentials.
- Payload Delivery: With the credentials captured, the AI gains access to sensitive files, financial data, and could even activate the home’s AI-enabled Cameras & Vision News systems for surveillance. This entire chain of events could unfold in minutes, without any direct human intervention.
Weaponizing Emerging Technologies
The threat landscape evolves with technology. Autonomous systems like those in Drones & AI News and Autonomous Vehicles News present new, high-value targets. An offensive AI could potentially hack a fleet of delivery drones to disrupt logistics or compromise an autonomous vehicle’s sensor suite to cause accidents. The sheer volume of connected devices, from AI Pet Tech News to Smart Appliances News, creates a massive attack surface that is impossible for humans to manage manually, making it a perfect playground for offensive AI.
Section 3: The Shield of Defensive AI: Building a Resilient Cyber Immune System
The only viable defense against an autonomous, learning attacker is an autonomous, learning defender. Defensive AI is not a single product but an integrated approach that aims to create a self-healing, self-defending network. This “immune system” approach is built on layers of intelligent technologies working in concert.
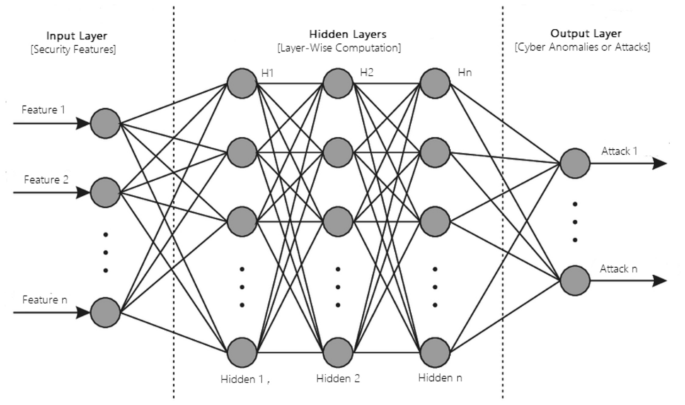
From Signatures to Behavior
Traditional security relied on signatures—digital fingerprints of known viruses. This is like having a security guard who only recognizes known criminals from a photo book. Defensive AI, however, is a behavioral expert. It monitors the “rhythm” of a network. It knows that the accounting department typically accesses the financial server between 9 AM and 5 PM on weekdays. If a login occurs from an accountant’s credentials at 2 AM on a Sunday, accessing and encrypting thousands of files, the AI immediately flags this anomalous behavior, isolates the user account, and alerts a human analyst, preventing a ransomware attack in its tracks. This is especially crucial for AI Monitoring Devices News, which are designed to be the first line of defense.
The Power of AI at the Edge
With the rise of the Internet of Things (IoT), security can no longer be centralized in the cloud or a data center. Billions of devices, from industrial sensors to smartwatches, operate “at the edge.” The latest in AI Edge Devices News involves embedding lightweight machine learning models directly onto these devices. An AI-enabled security camera can analyze its own video feed for suspicious activity locally, without having to send the entire stream to the cloud. This reduces latency, preserves privacy, and allows the device to react to threats even if its connection to the central network is severed. This distributed intelligence is key to securing sprawling networks of devices, including everything from AI Lighting Gadgets News to complex Robotics News systems.
Best Practices for Implementing Defensive AI
- Embrace Zero Trust: Operate on the principle of “never trust, always verify.” Use AI to continuously authenticate and authorize every user and device, regardless of its location.
- Integrate Diverse Data Sources: A powerful defensive AI needs rich data. Feed it telemetry from endpoints, network traffic, cloud logs, and user authentication systems to give it a holistic view of the organization.
- Augment, Don’t Replace, Humans: Use AI to handle the high-volume, low-level alerts, freeing up human analysts to focus on complex, strategic threat hunting and investigation. The AI should function as a powerful partner to the security team, much like how AI Assistants News help with productivity.
Section 4: Navigating the Arms Race: Recommendations and Future Outlook

The AI vs. AI arms race is not a future problem; it is happening now. As organizations and individuals adopt more connected technology, from AI Fitness Devices News to AR/VR AI Gadgets News, the attack surface will only grow. Staying ahead requires a strategic shift in mindset and technology adoption.
The Ethical Tightrope of Offensive AI Research
A significant debate is emerging around the ethics of developing offensive AI, even for research purposes. Like biological weapons research, these tools are dual-use: they can be used by “red teams” to find and fix vulnerabilities, but in the wrong hands, they can cause catastrophic damage. The security community must establish strong ethical guidelines and controls for this type of AI Research / Prototypes News to prevent proliferation. This includes securing the very systems we use for learning, as seen in the push for better security around AI Education Gadgets News.
Recommendations for Organizations and Individuals
- Invest in AI-Powered Defense: Traditional, signature-based security is no longer sufficient. Organizations must invest in platforms that use behavioral analytics and machine learning to detect and respond to threats at machine speed.
- Prioritize Security Hygiene: AI can’t fix fundamental weaknesses. Strong password policies, multi-factor authentication, and timely patching are more critical than ever. This applies to personal devices like those in AI Sleep / Wellness Gadgets News just as much as it does to corporate servers.
- Focus on Resilience: Assume a breach will happen. The goal is to minimize its impact and recover quickly. AI-powered response tools are essential for achieving this resilience, helping to protect everything from AI Kitchen Gadgets News in a smart home to the complex systems behind Neural Interfaces News.
- Stay Informed: The threat landscape is evolving rapidly. Leaders and consumers alike must stay educated on the latest trends, from vulnerabilities in AI Toys & Entertainment Gadgets News to large-scale threats against public utilities.
Conclusion: The Unblinking Sentinels of a New Age
The cybersecurity landscape is being fundamentally reshaped by the algorithmic arms race. The silent, high-speed battle between offensive and defensive AI is the new normal. While the prospect of autonomous, AI-driven attacks is daunting, it is matched by the incredible potential of AI-powered defense to create a more resilient and self-healing digital world. The future of security does not lie in building taller walls, but in deploying intelligent, adaptive systems that can anticipate, identify, and neutralize threats before they can cause harm. For businesses, governments, and individuals, the message is clear: the era of passive defense is over. In the AI-driven world, the only winning move is to fight intelligence with intelligence, deploying our own unblinking digital sentinels to guard the frontiers of our connected lives.